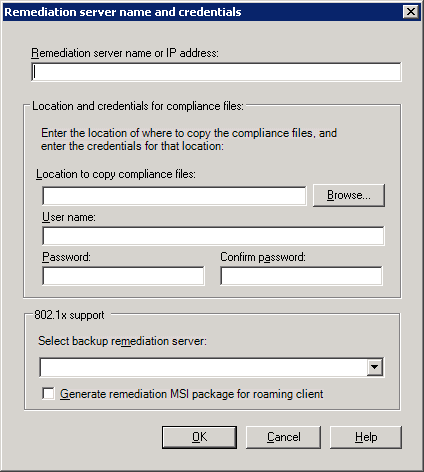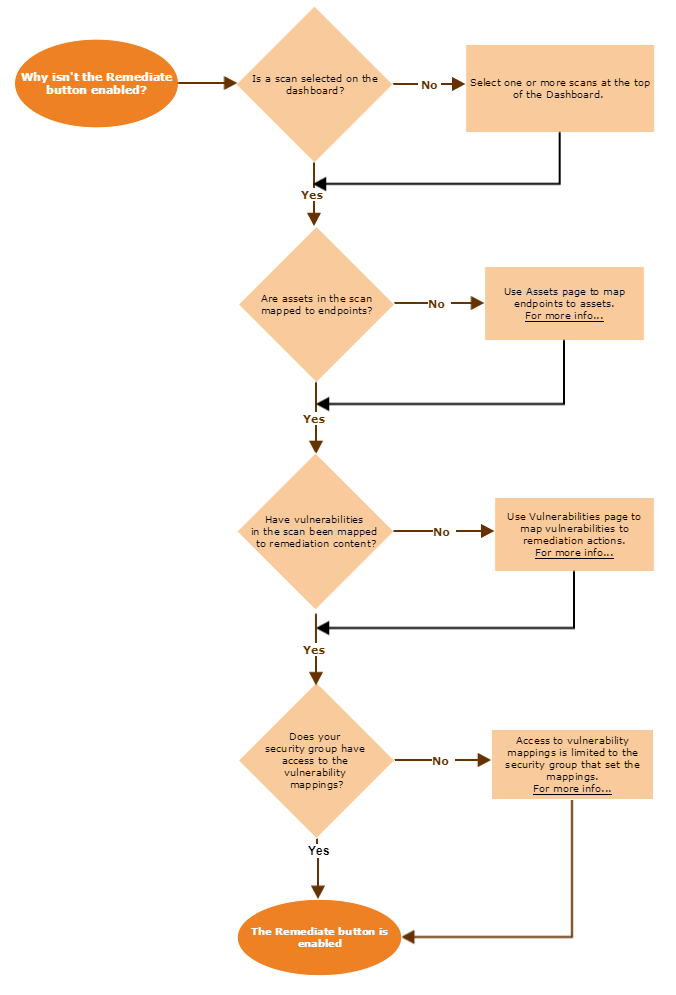
Creating a Remediation operation for TrueSight Server Automation - Documentation for TrueSight Vulnerability Management 3.1 - BMC Documentation

Choosing remediation targets and patches for AIX - Documentation for TrueSight Server Automation 23.1 - BMC Documentation
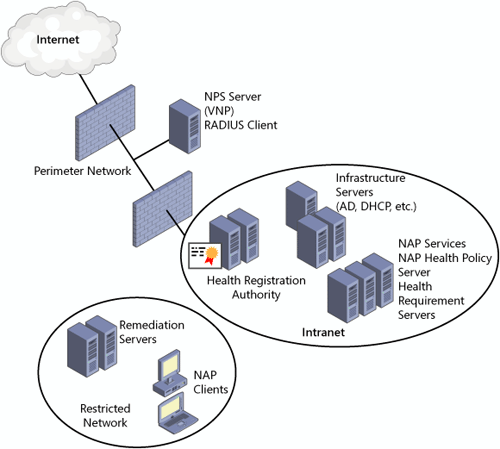
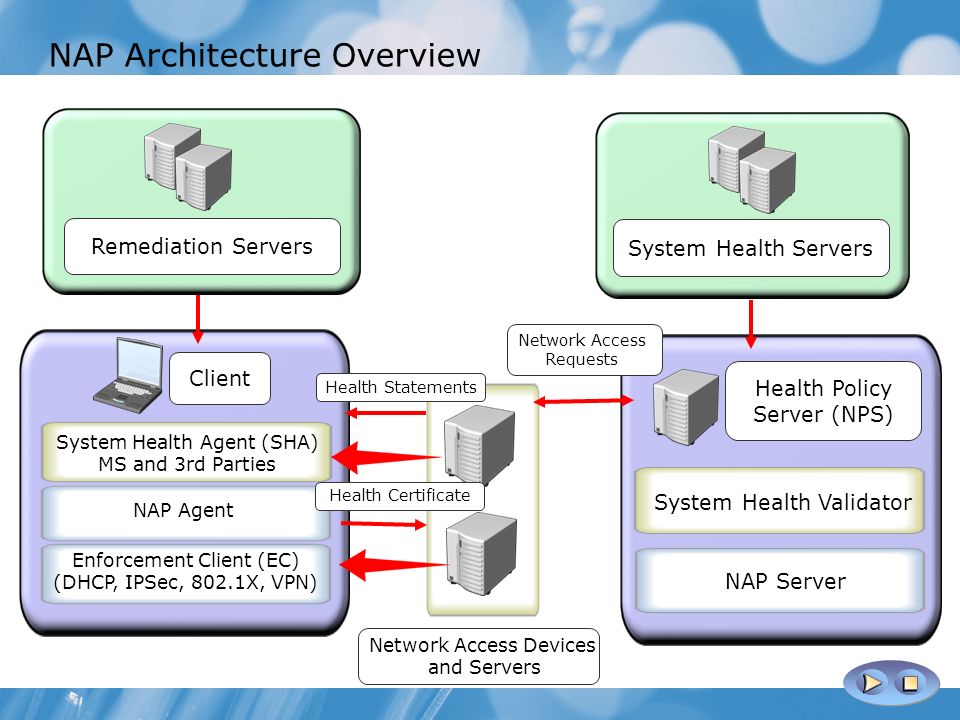
Windows Server : Network Access Policy and Server and Domain Isolation (part 1) - Network Access Protection Overview - Windows Server - tutorial.wmlcloud.com

Creating a Remediation operation - Vulnerability Manager - Documentation for BMC BladeLogic Portal 2.2 - BMC Documentation