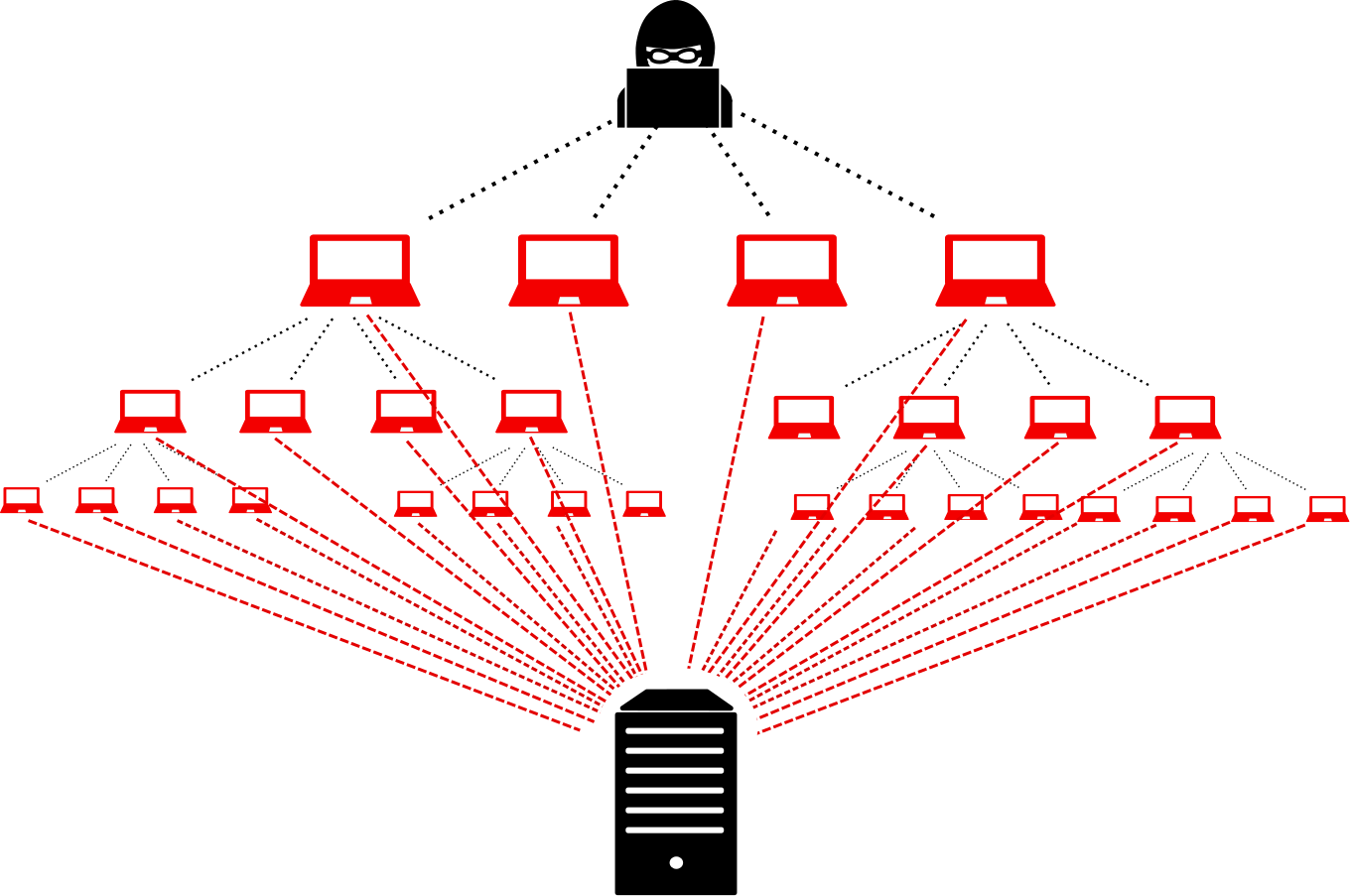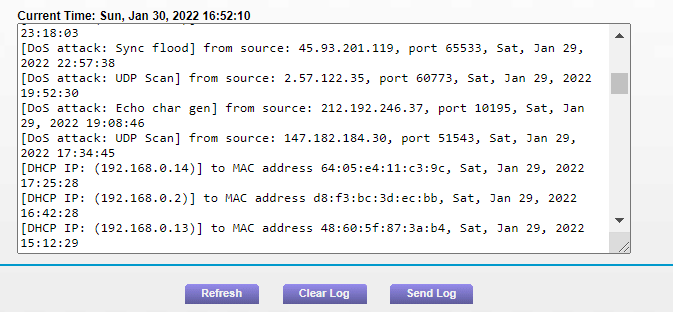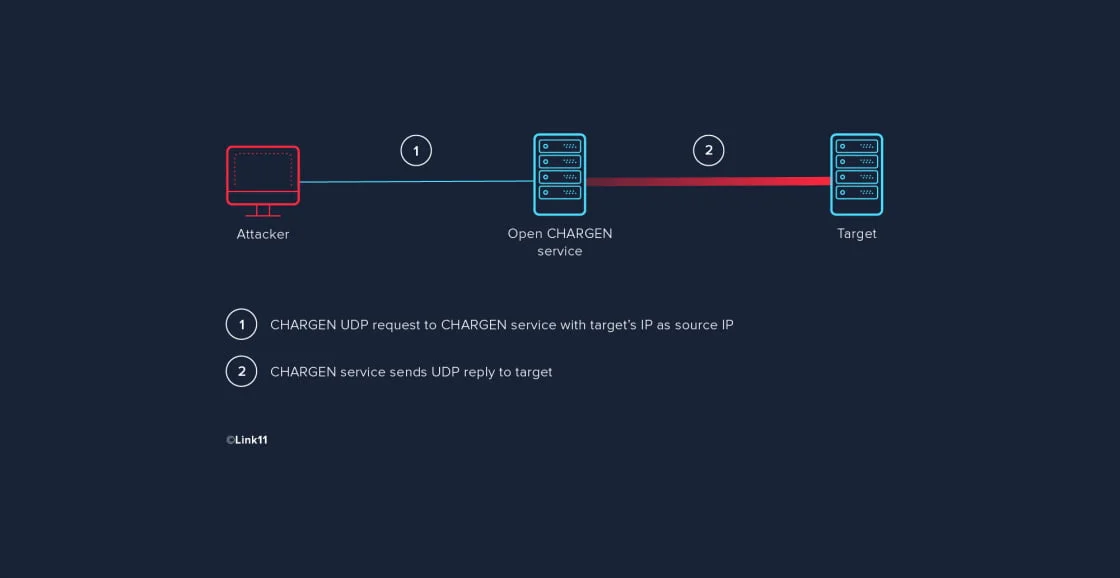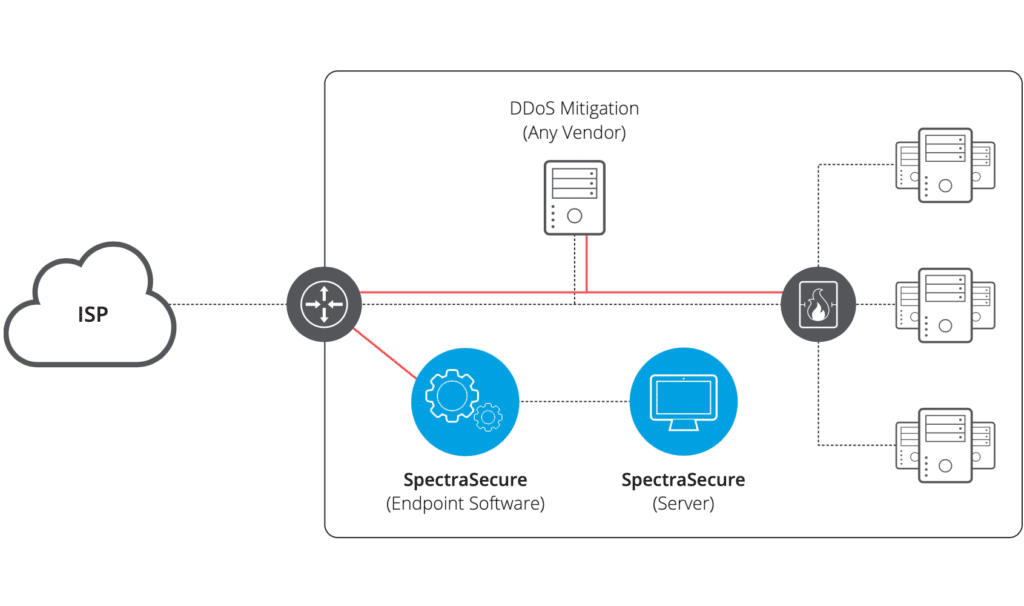
JSAN | Free Full-Text | DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges

JSAN | Free Full-Text | DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges

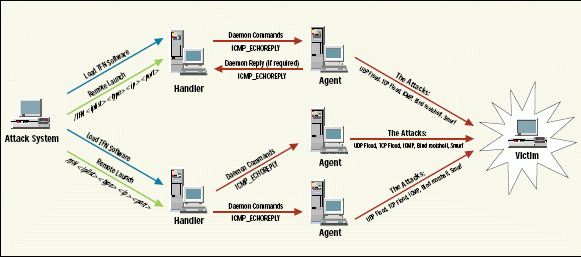
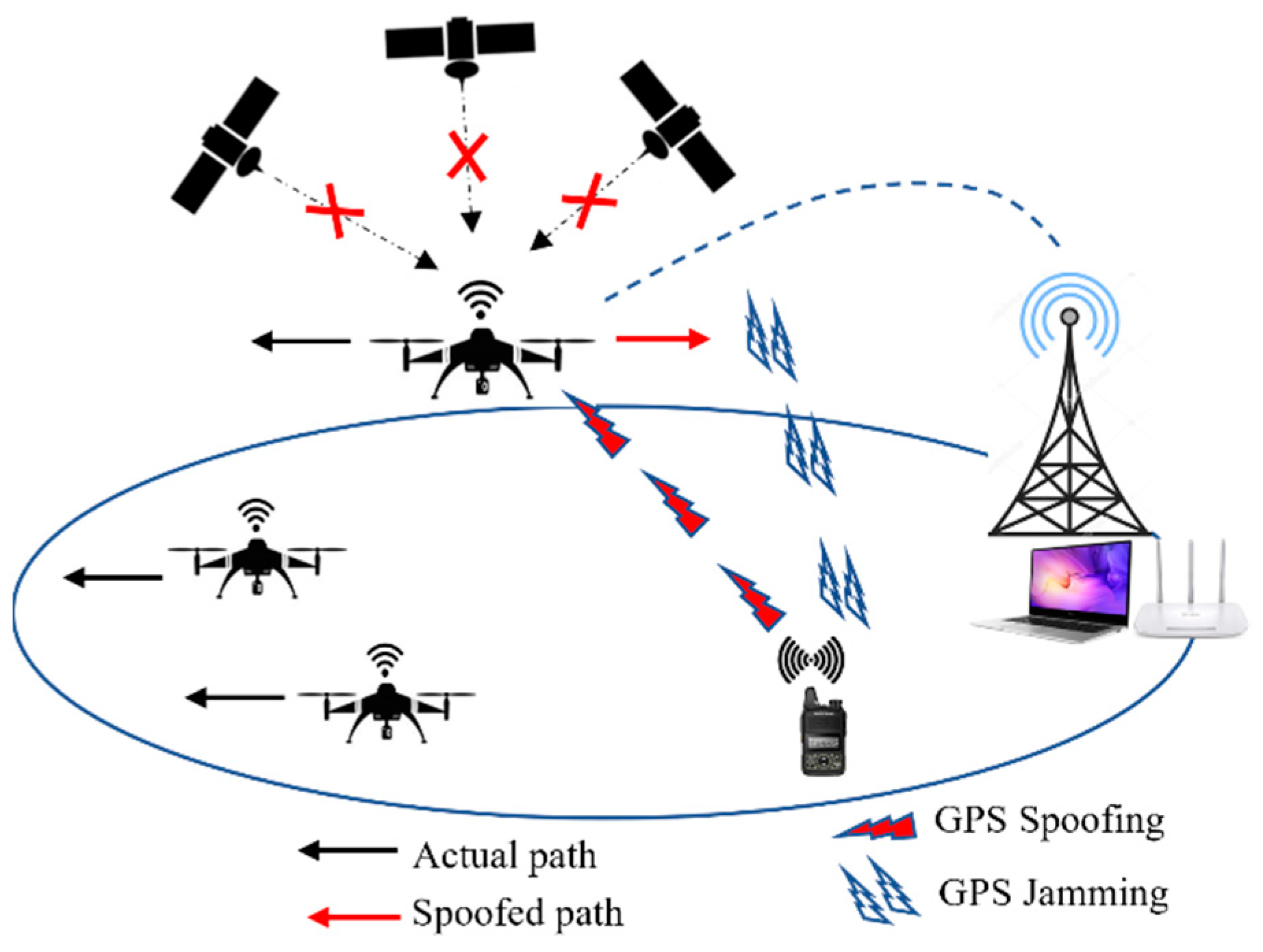
DDoS attacks and machine‐learning‐based detection methods: A survey and taxonomy - Najafimehr - Engineering Reports - Wiley Online Library

Understanding Defense Against UDP Flood Attacks - CloudEngine S16700 V600R022C10 Configuration Guide - Security - Huawei

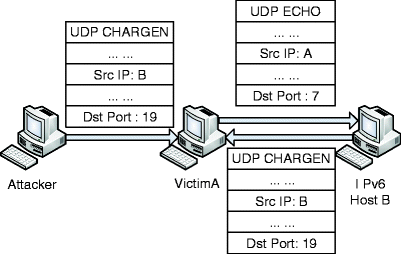
SOLVED: Explain how each of the following attacks occur: Ping flood, Smurf attack, Echo-Chargen, Teardrop attack, DNA spoofing, Rerouting routing, Session Hijacking, Distributed denial of service. List six types of firewalls.

Security Breaches. Security Breaches Some terminology Guiding principle is CIA: Confidentiality Integrity Availability Often, these are conflicting. - ppt download