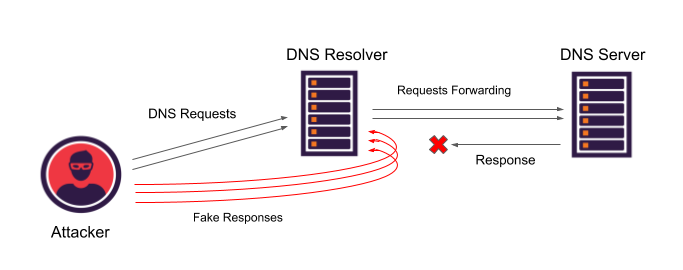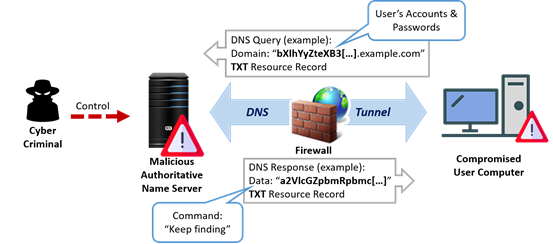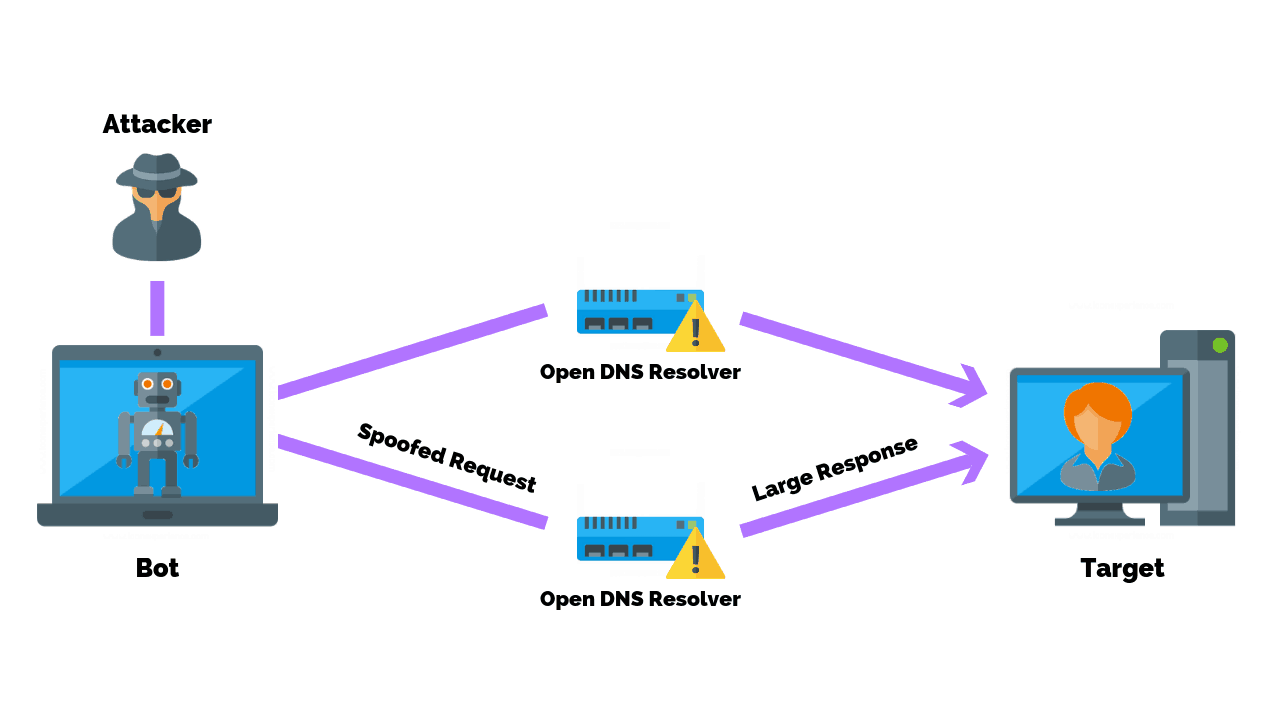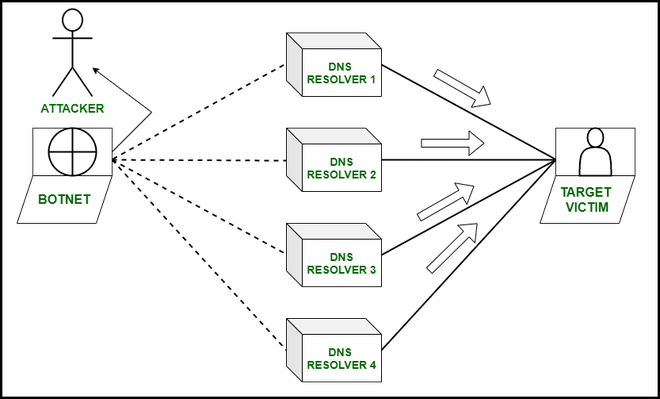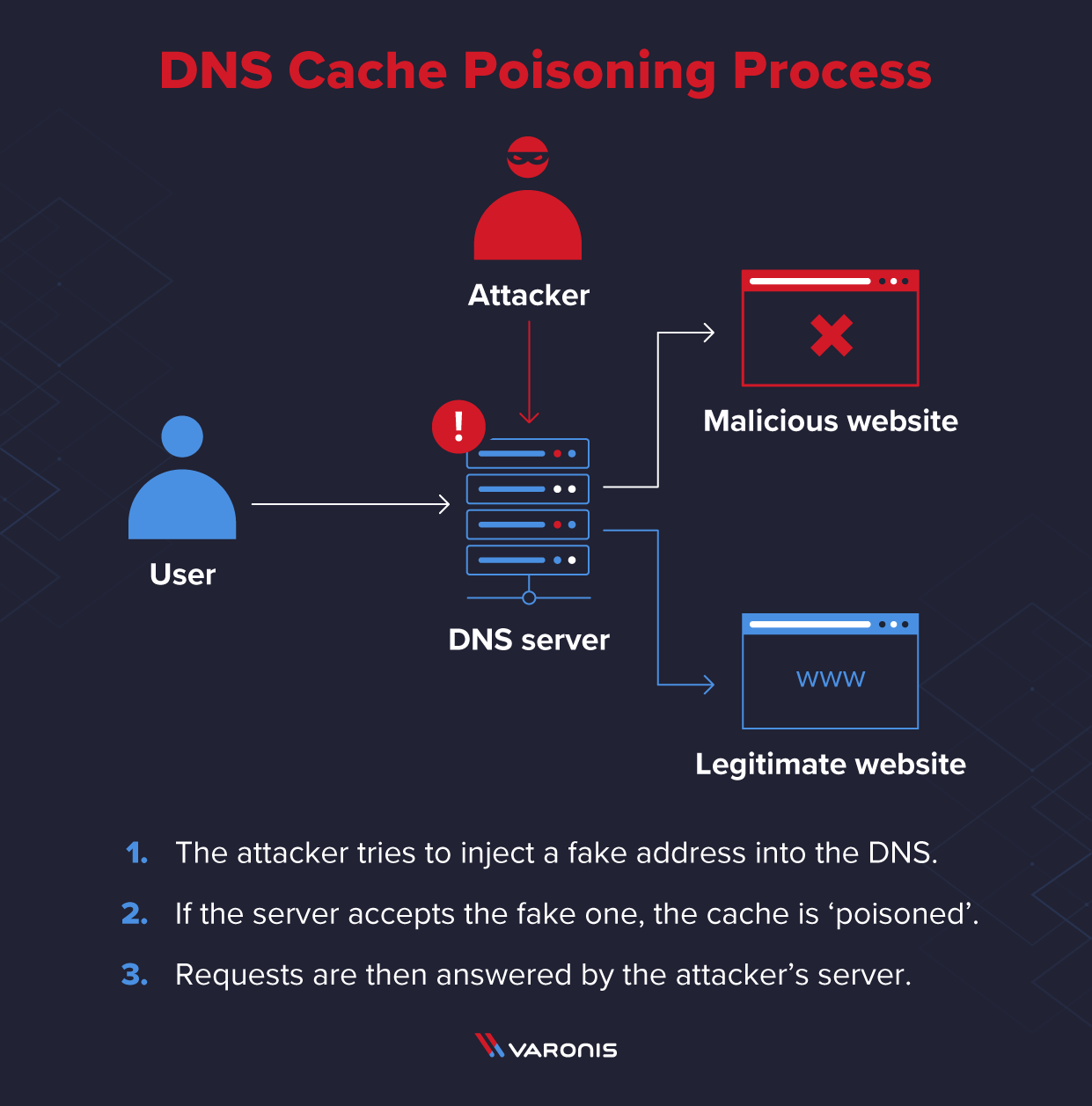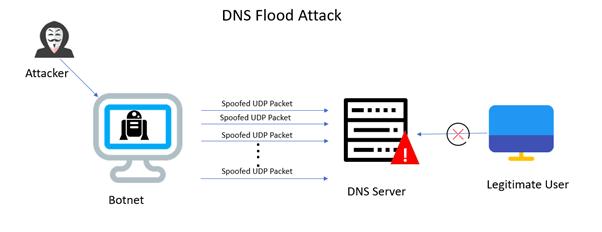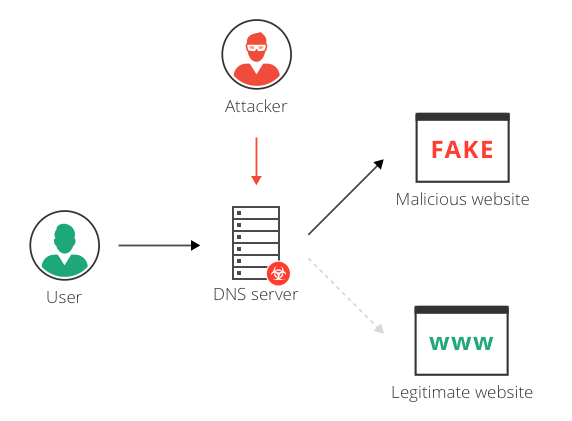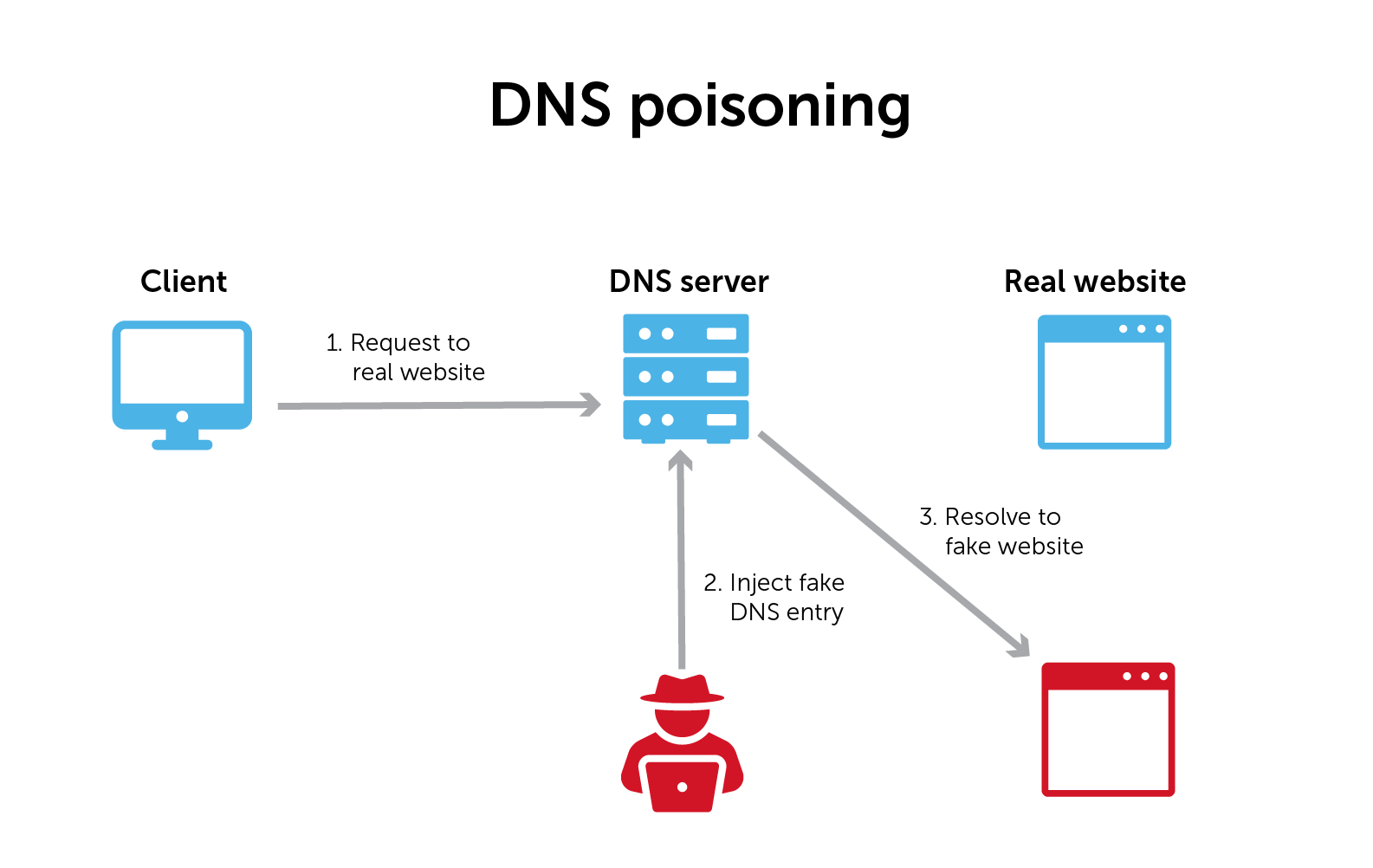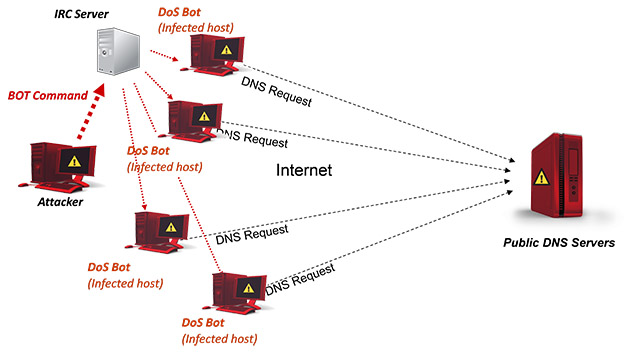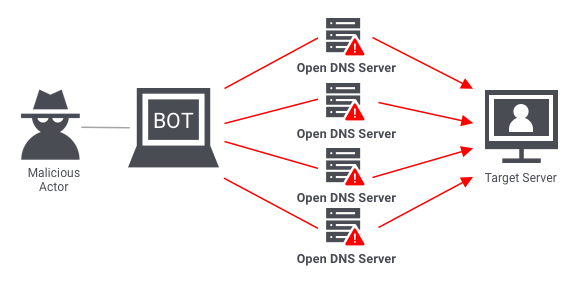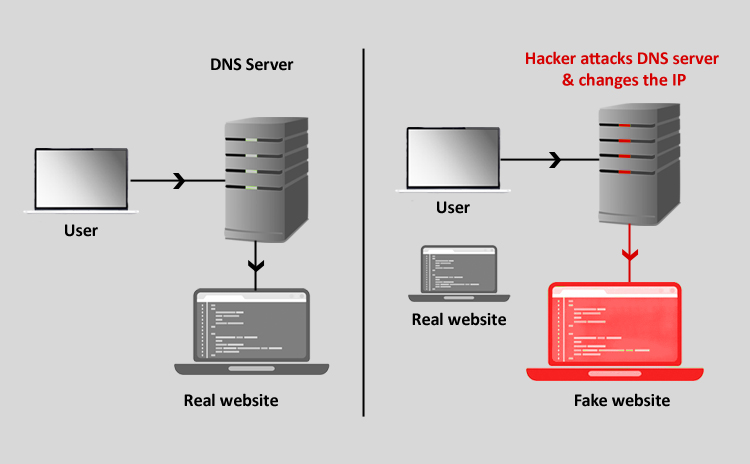
Cyber Attacks Explained - DNS Invasion - Cyber Security Blogs - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata India Dubai Bahrain
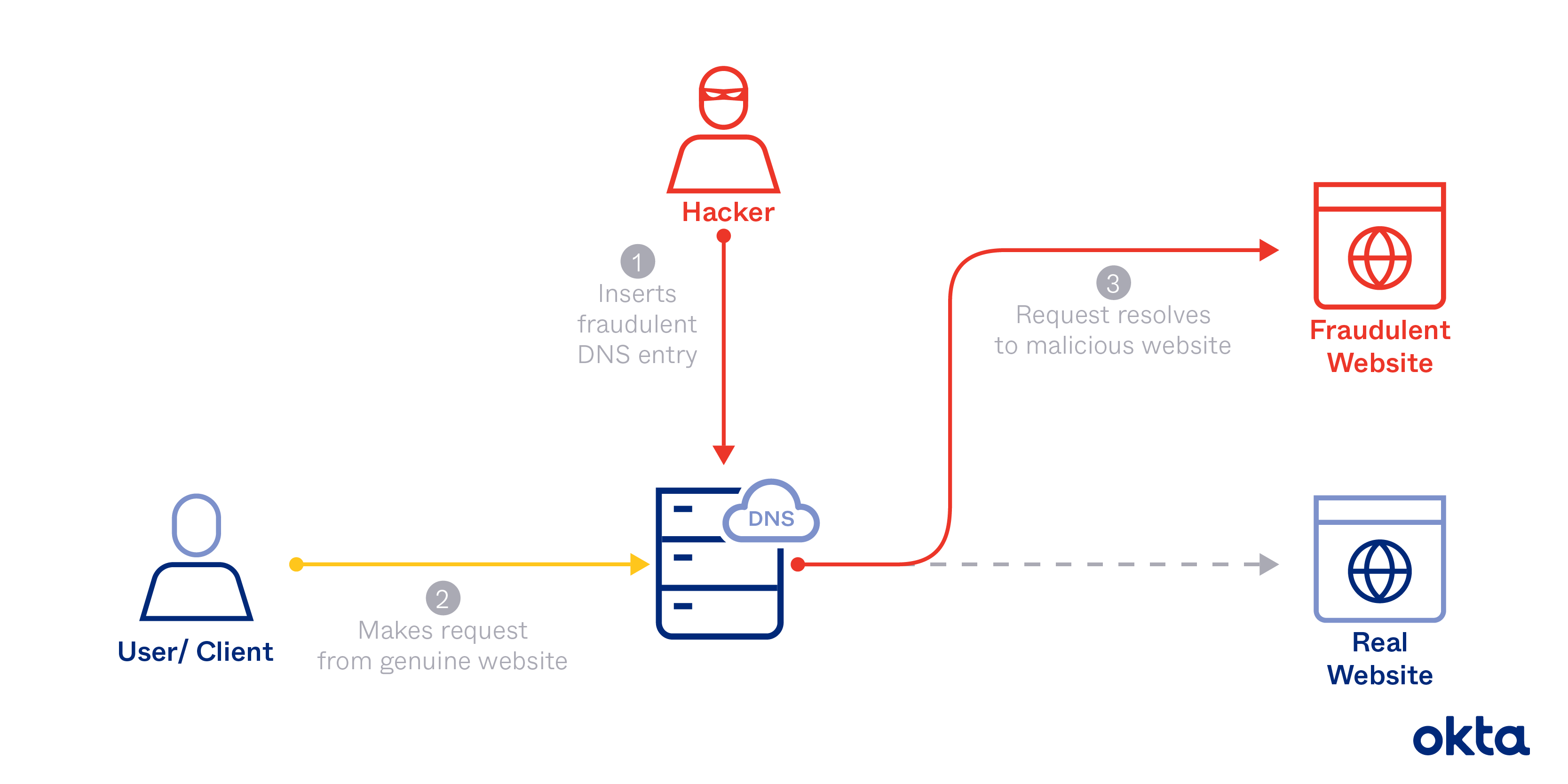
Dns attack with MITM Domain Name System (DNS) is the protocol of web... | Download Scientific Diagram